1. Increase in Wi-Fi devices and amount of user’s
data on the network
Number of wireless devices connecting to a public wireless hotspot
networks are multiplying day by day. The main reason behind this increase of
devices can be attributed to growing base of mobile users carrying multiple
wireless gadgets such as smartphone, iPad, and notebook, wherever they roam. In fact, today’s internet users are going
through a paradigm shift as they are always wanted to be connected to the
internet. This has resulted into exponential growth in user’s data on the
wireless hotspot networks. A lot of free
Wi-Fi internet service providers have to cope-up with the demand for additional
bandwidth required to handle the sudden growth of user’s data on their network.
2. Demand for throughout coverage
Since transmit and receive range of smartphones and other similar
handhelds are less compared to laptops, new coverage holes are getting created
in an already deployed conventional Wi-Fi hotspot network. Service providers are under intense pressure to provide throughout coverage, for example in hospitality
industry where guests need to have Internet access not just in rooms but also
in passage, terrace etc.
3. Digital certificate cost
In conventional Wi-Fi hotspot, authorized access to the Internet access
is provisioned using a web based login portal. Providing user authentication
without application layer security is a serious security threat to a service
provider. Awareness about the insecurity of open Wi-Fi configuration is growing
fast and hence application layer user authentication control can be easily
bypassed. Therefore, service providers have to also bear the cost of digital
certificate required by https based user authentication procedure.
4. Unwanted connected device handling
Today’s
hotspot infrastructure is churning out as it is unable to deliver desired
performance due to large number of wireless clients connecting to the network,
causing network to reach its maximum capacity soon. Under such condition,
wireless hotspot infrastructure has no inbuilt intelligence that can help
differentiate between a paid and unpaid user and hence when the number of
clients exceeds the connection limit, even paid users have to suffer. Problem
like this is affecting the revenue from fee based wireless hotspot service.
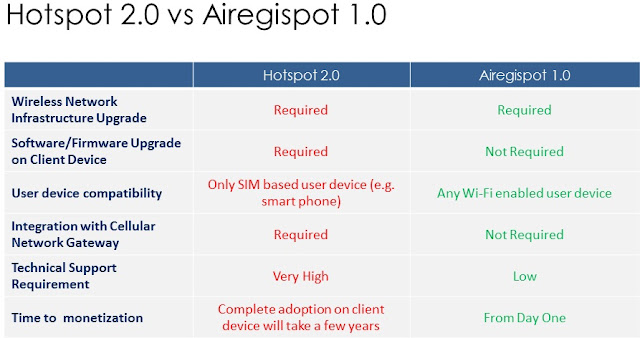
5. HS 2.0 integration overhead
In
order to provide support for roaming customers, a new technology called Hotspot
2.0 (HS2.0) is being adopted by the wireless broadband industry. In order to
support HS 2.0 WISPs need to upgrade their wireless hotspot infrastructure. The
technology also requires integration with cellular service providers in order
to support SIM card based user authentication. This is probably ok for carriers who are creating
their own wireless hotspot infrastructure to support data offload. Wireless
service providers already having hotspot running need to shell out additional
cost in order to bring support for user authentication required in HS2.0. On contrary to this, wireless user base is still not ready to use the
technology as it requires software/firmware upgrade on client device, which can
be a big barrier to HS2.0 based service monetization.
The cost of running a Wi-Fi hotspot service is growing while
the revenue from the service is not showing similar growth sign. Airegis solution for Wi-Fi hotspot enables
wireless service providers to run a truly secured wireless internet service
that can be offered to hotspot users as value added premium service. Apart from
providing privacy and over-the-air data protection, the most attractive
advantage of Airegis powered wireless service is that network connectivity, authentication, and
network usage policy are clubbed together into one that helps next generation smartphone user in getting a
quick access to the Internet. The inbuilt
intelligence of the Airegis powered Wi-Fi hotspot system allows only authorized
device to connect and use the service. This helps in keeping the wireless
network resource available for those who have subscribed to premium wireless service. The cost of digital certificate needed for conventional
captive portal authentication can be also saved as with layer-2 security based wireless system, need
for a secure web authentication becomes redundant.
In short, by embracing Airegis powered Wi-Fi hotspot
solution, wireless internet service providers can easily beat new challenges of
next generation wireless hotspots.